Cyber threats are on the rise and if an online driven company does not set up adequate security to its operations it is bound to collapse. Normally as a computer user you will detect a malware when it has already caused damage to your system. There is a new crop of sophisticated online attacks which attacks your system in bits, these attacks are hard to detect and prevent even with normal protection programs. FireEye through its threat detection and prevention across multiple online platforms such as Analytics, Network, Endpoint, Mobile, Forensics, Email and Content the company has established itself as a reputable cybersecurity company throughout the globe.
FirstEye is the first cybersecurity firm of its kind to be certified by the U.S Department of Homeland Security. The company has investigated high-profile attacks against giant firms such as JP Morgan Chase and Sony Pictures. With operations across 67 countries and the fastest growing cybersecurity firm according to Deloitte, FireEye has proved to be the leading player in malware protection systems. This article will take a look at FireEye, its products and its role in IT security as a whole.
Growth of FireEye
Through its major acquisitions of Mandiat, nPulse technologies, and iSIGHT Partners, FireEye has been able to diversify its services and products, through Mandiat its consulting arm FireEye offers Analytics and Forensics which provide deep visibility and automates responses to security breach incidents. nPulse has developed FireEye’s ability to single out intrusions in an organization’s network by simplifying the intrusion tracking process at the same time analyzing and understanding the effect of the intrusions on the network. The acquisition of iSIGHT Partners has greatly improved the IT security intelligence.

FireEye Products and services
FireEye has developed a set of creative and problem-oriented products which are designed with great information concerning IT security needs. The Central Management System and the Dynamic Threat Intelligence are two products which have provided the much-needed cybersecurity to many users across the globe.
Central Management Systems (CMS) greatly centralizes the management, reporting and the data sharing of Email MPS, File MPs, Web MPS and even Malware Analysis System into one appliance that is network-based. The Central Management System does so by acting as a single distribution source for all IT security intelligence. Through the FireEye Threat Intelligence, most security products from FireEye can be able to actively block potential malware files on mobile devices and network endpoints.
The IT security service from FireEye has three levels; Advanced Threat Intelligence Plus (ATI+), Advanced Threat Intelligence (ATI) and the Dynamic Threat Intelligence (DTI). These three services only differ on the detail of reports sent to you and also the number of services included in each level. Dynamic Threat Intelligence (DTI) is a machine to machine connection that detects and responds when connected to the FireEye IT security products. Advanced Threat Intelligence (ATI) brings on the aspect of context; context is a key aspect in cybersecurity because it gives a direction and sense in which to conduct threat analysis. Advanced Threat Intelligence plus (ATI+) widens the protection with a storage location for research that materially contributes to an improved effectiveness of threat and malware analytics.
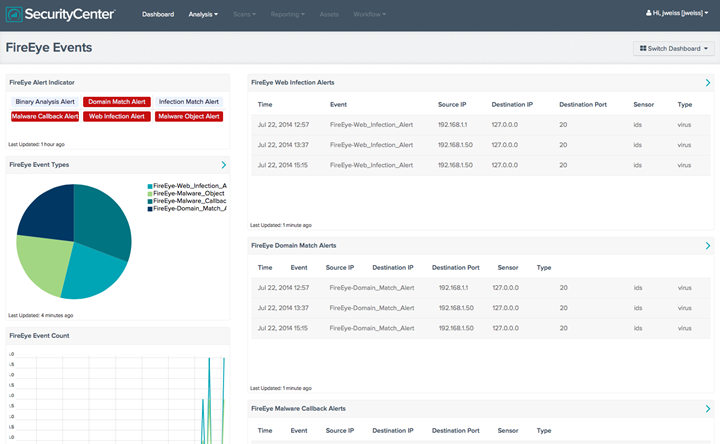
The FireEye Intel Centre is a portal that offers IT Security Consulting services to users who are in need of direct threat intelligence from the FireEye team. The direct intelligence from the FireEye team of professionals gives the customers the unique ability to document, carry out proper management and then share their own intelligence and experience with other customers. This interaction between different users and/or customers offers them with quality IT Security Consulting services; in this process, they are equipped with rich information concerning detection and prevention of malware files and threats.
The intelligence from other users is obtained from their own experiences; this intelligence can offer workable solutions to other users under the same threatscape.
In the Intel Centre, the FireEye system continually creates and updates encyclopedia entries of new threats and malware files as well as hostile addresses. These new threats are researched and analyzed; the process carried out through which the powerful FireEye sandbox which offers detailed and complete output and adds important knowledge to the users as well as the analysts.